30 Recommended Suggestions For Choosing A Dubai Cyber Security Service
Wiki Article
Top 10 Ways To Assess The Certifications And Compliance Of A Cybersecurity Services Firm In Dubai.
1. Verify Certification AuthenticityBegin the process by confirming the validity of your company's certificates. Verify that the certificates are valid and current by contacting the issuing authority or the body that certifies them. For instance, ISO 27001 is a crucial certification to look into. Certifiable certifications provide proof of adherence with recognized cybersecurity standards.
2. Understanding Local Regulatory Compliance
Find out about the UAE Cybersecurity Strategy and the UAE Data Protection Law. Make sure that your company is adhering to the legal guidelines. If not, there can be legal repercussions.
3. Assess Industry-Specific Standards
Depending on what industry you work in, specific standards may be more appropriate for your. For instance healthcare and financial institutions companies should be focused on PCI DSS. Examining certifications for specific sectors ensures that the company has the right expertise in tackling specific sector risks.
4. Request Documentation
Request comprehensive documentation demonstrating conformity to the applicable standards. You can ask for audit reports along with security policies and guidelines for risk management. These documents will provide you with more insight into how committed the organization is to cybersecurity and compliance.
5. Inquire About Third-Party Audits
Find out if the business is subject to regular audits from third parties. Independent audits can offer an objective evaluation of the company's compliance status and security practices. Seek out audit reports from credible companies that can verify the firm's security practices.
6. Evaluate Continuous Improvement Initiatives
Security continues to evolve and businesses need to demonstrate a commitment towards continuous improvement. You can check if the company regularly updates their policies and technology so that they can adapt to regulatory changes and new threats. This may require ongoing security updates and training.
7. Examine Employee Training Programs
The effectiveness of a cybersecurity strategy is determined by the competence of its employees. Inquire about the company's training programs that focus on security best practices and compliance. Training sessions regularly scheduled will keep employees updated of the most recent threats, compliance requirements, and best methods.
8. Review Incident Response Plans
Know the company's incident response procedures. A solid plan for responding to incidents should explain how the company deals with data breaches. Make sure you check their protocols comply with the compliance requirements as well as best practices.
9. Find testimonials from customers and refer to references
Ask for references from current clients who have attested to the certifications and compliance of the company. Testimonials provide insight into the reliability of the company and effectiveness in managing cybersecurity risks. They can help to assess their standing within the field.
10. Research Industry Recognition
Look into the company's reputation in the cyber-security world. Look for awards, recognitions or memberships in professional associations that highlight their commitment to cybersecurity and compliance excellence. A strong reputation is usually associated with the reliability and competence of their staff. See the most popular Cybersecurity Company in UAE for more advice including data secure, security solution, network security and cyber security, it security description, cyber security in companies, business and cybersecurity, managed cyber security services, careers in cyber security, managed security, cyber & network security and more.
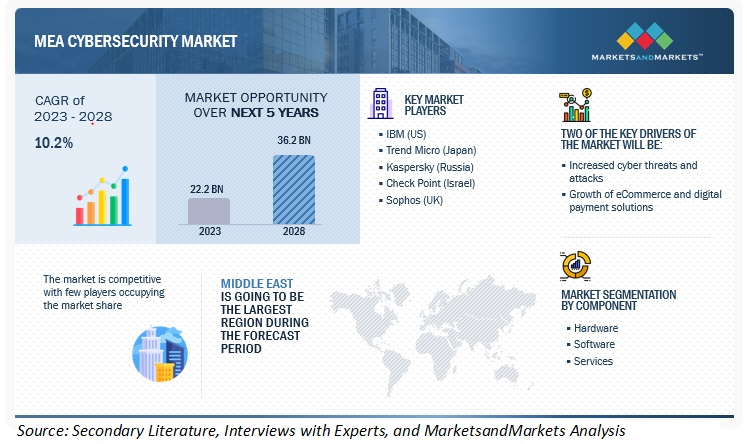
Top 10 Tips To Evaluate The Capabilities Of Incident Response In The Cybersecurity Services Business
1. Begin by analyzing the incident response framework your business has in your place. A well-defined framework, like the NIST Cybersecurity Framework or the SANS Incident Response Process, shows that the business follows the best practices of the industry for handling incidents efficiently. They should have a systematic approach to handling incident.
2. Evaluate Incident Response Team Expertise
Check the credentials and experience of the incident response team members. Examine for certifications, such as Certified Incident Handlers (GCIH) and copyright Security Professionals (copyright). Team members who are well-versed in the area of incident handling and mitigation can effectively manage and reduce the risk of incidents.
Review past Incident Case Research
Ask for instances or case studies of previous incidents handled by the company. Analyzing how they respond to actual scenarios can provide an insight into their effectiveness as well as their speed and general approach to handling incidents. Find out in detail the methods they used to identify, contain or resolved issues.
4. Make sure you check for 24-hour Incident Response availability
Check if they have 24 hour emergency services. An incident involving cybersecurity can happen anytime. A team that is always available will help minimize damage, while also minimizing recovery time.
5. Request information about tools for detecting incidents
Assess the tools and technologies the company employs for monitoring and detection of incidents. Effective detection tools, such as Security Information and Event Management (SIEM) systems, as well as intrusion detection systems (IDS) are crucial for identifying potential security threats quickly and precisely.
6. Examine Communication Protocols
Find out the procedures for communication the company employs in the case of an incident. Clear and effective communication is essential for coordinating response to inform stakeholders, as well as making sure that everyone is aware of their roles during an incident. Be aware of how they keep customers informed throughout the response process.
7. Review of Post-Incident Review Procedures
Find out about the post-incident reviews that are conducted by the company. It is crucial to conduct thorough review following an incident to discover any lessons that can be learned. To improve future response efforts, look for businesses that have made changes on the basis of these reviews.
8. Evaluate the effectiveness of recovery strategies and methods for remediation.
Knowing the methods the business employs to restore and repair after an incident is crucial. Recovery plans must contain the steps to recover data and systems and ensure that vulnerabilities are addressed in order for future incidents to be prevented. Ask about their strategy for recovering systems and securing them post-incident.
Examine the Compliance with Regulations
Check that your ability to respond to incidents is in line with the applicable regulatory requirements. Based on the type of business you operate in, there may be specific rules regarding incident reporting and response. It is essential to find a business that is aware of these laws in order to comply.
10. Ask for references and testimonials
In order to gather references, inquire with existing customers whether they've ever utilized the company's services. Client testimonials can provide valuable insights into their effectiveness and reliability as well as overall satisfaction with the services offered during an incident. Take a look at the top penetration testing company in uae for blog examples including data secure, network security, network security and cyber security, managed security, business and cybersecurity, cyber security tools, cyber security tools, network and security, technology and cyber security, cyber security info and more.

Top 10 Tips On How To Evaluate Tailored Solutions From Cyber Services Companies
1. Find out the abilities of the business to create customized cybersecurity solutions that meet your specific requirements. Find out how the company can tailor services to meet your business's size, industry and specific dangers. One-size-fits-all is not going to meet your needs.
2. Needs Analysis Process
Ask about the process that the company employs to conduct a needs analysis. A thorough needs analysis should consist of understanding your current circumstances, identifying your vulnerabilities, and determining what you need. The solutions they offer will be more compatible with your requirements if they conduct an in-depth analysis.
View Previous Tailored Solutions
Examples or cases which show how the business has tailored its offerings for previous clients are a good idea. Analyzing these cases will provide insight into the capability of the firm to adapt its offerings to various contexts and how effective their customized approach is.
4. Understanding Industry Specific Solutions
Make sure the company has solutions that are specifically tailored to your industry. Financing, healthcare and retail each have their own unique cybersecurity problems. These solutions are tailored to meet the knowledge and understanding of the company of your particular industry.
5. Examine the flexibility of Service Offerings
Check how flexible the organization can be in the way of changing their service offerings. For effective cybersecurity it is essential to be flexible enough to adjust services as your business grows and as the threat environment alters. Ensure they are willing to adjust their solutions over time.
6. Examine Integration with Existing Systems
A company's capability to integrate customized solutions with the existing IT infrastructure is important. Integration is the key to ensure that the new security features function effectively without disrupting the operation.
7. Look for custom reports and Analytical Tools
It is also important to determine whether the business can provide you with customized reporting and analytics aligned to your objectives. Custom reports can help you track the effectiveness of security measures, and make informed decisions regarding your security strategy.
8. Collaborative approach to assessment
Check the company's willingness and ability to work together with your staff. A collaborative approach ensures that the tailored solutions are not just efficient but also fit with the culture of your organization and operational procedures. Find companies that emphasize communication and collaboration.
9. For more information on the scalability of solutions, contact us.
Make sure that the solution is scalable. As your company grows or evolves, your cybersecurity requirements could change. You must ensure that the cybersecurity solutions of your company are easily scaled up or down without major changes.
10. We invite feedback from our clients about Tailored Service
Find feedback from your current customers on how they feel about the customized solutions provided by the business. Testimonials give valuable insights on how the company responds to particular requirements. They can also reveal how satisfied clients are with the tailored services. Take a look at the most popular iconnect for site advice including security in data, information and cyber security, cybersecurity and ai, network and security solutions, network security management, ai in cybersecurity, security ot, network security systems, cybersecurity and business, it security jobs and more.
